Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
S&P Global Offerings
Featured Topics
Featured Products
Events
Financial and Market intelligence
Fundamental & Alternative Datasets
Government & Defense
Professional Services
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
Financial and Market intelligence
Fundamental & Alternative Datasets
Government & Defense
Professional Services
Banking & Capital Markets
Economy & Finance
Energy Transition & Sustainability
Technology & Innovation
Podcasts & Newsletters
Research — 4 Oct, 2022
Introduction
One of the foundational elements of establishing effective "data culture" is to ensure that the maximum number of workers can drive business value from data in their daily roles. Yet even within the walls of the organization, it can be difficult to do this while carefully balancing risk and appropriate use of data. In 451 Research's Voice of the Enterprise: Data & Analytics, Data Management & Analytics 2021 survey, 29.3% of respondents reported that "security/access control for self-service data" was one of the biggest challenges affecting the delivery or adoption of self-service models at their organization — a top three response.
With such pertinent governance and security challenges facing organizations as they try to leverage data resources internally, it would follow that securing data outside the walls of the enterprise would be even more difficult as businesses seek to share datasets with parties such as partners and suppliers. However, today, organizations appear relatively confident in their ability to securely exchange data externally. Perhaps this is hubris — or conversely, a harkening to the reality of the normalcy of secure external data exchange practices on the rise.

Across industries, business data — and its effective ongoing leverage — has often become the competitive "secret sauce" that sets market leaders apart from market laggards. Sensitivity is no longer just confined to traditionally restricted documents or sources related to IP or customer information but extends to nearly all business data that could potentially provide insight into how the business operates. In this sense, exchanging data with external parties is fraught with additional risk. Yet businesses today have more partners, suppliers and third parties than ever before. The ability to securely exchange data with these external parties is becoming a matter of competitive edge. So while organizations today seem relatively confident in their ability to securely exchange data externally, some of this may be overconfidence, especially given the state of most internal data governance and data access control programs. If the organization cannot effectively control its data internally, it is unlikely it can do so effectively outside its walls.

What is a program for secure exchange of data with external parties?
Secure data exchange, broadly speaking, allows an untrusted or less-trusted party to perform processing or other actions on a dataset in a highly controlled way in a manner designated by the originating party. This often works by applying data security mechanisms so that groups of data consumers with differing rights and permissions can work from and leverage the same datasets, with access and visibility that is strictly appropriate for them.
Secure data exchange, of course, can occur within the walls of a single organization, such as between departments or roles that may have differing rights for specific datasets. For example, an HR department may have unrestricted access to all employee personal data yet may need to securely share partially obfuscated subsets of that data with other departments for functions such as payroll to be processed.
Securely exchanging data with external parties applies these principles to the transfer and sharing of data outside the walls of an organization. Often more so than data exchange within the organization, data exchange and sharing outside of the organization is fraught with additional competitive risk because it can be more challenging to control the visibility and processing of data once it has left the control of the originating organization.
In this sense, theoretically, securely exchanging data outside of the organization should go well beyond mechanisms for secure transfer from point A to B. However, it is unclear whether most organizations engaging in "secure external data exchange" have reached this higher level of sophistication.
Enterprise confidence in secure data exchange is high but varies based on demographic
Overall, 70% of respondents from 451 Research's Voice of the Enterprise: Data & Analytics, Data-Driven Practices 2022 survey report that their organization has a program for securely exchanging data with external parties, but this varies significantly based on demographic. Respondents can broadly be split into two camps depending on how much their organization bases strategic decisions on data. In our overview of survey findings, those that report their organization bases "nearly all" or "most" strategic decisions based on data are deemed data drivers, while those that report their organization bases only "some" or "few" strategic decisions based on data are deemed data drifters.
In this conceptual model, data drivers are much more likely than data drifters to report having a program to securely exchange data with external parties.
In this conceptual model, data drivers are much more likely than data drifters to report having a program for the secure exchange of data with external parties.
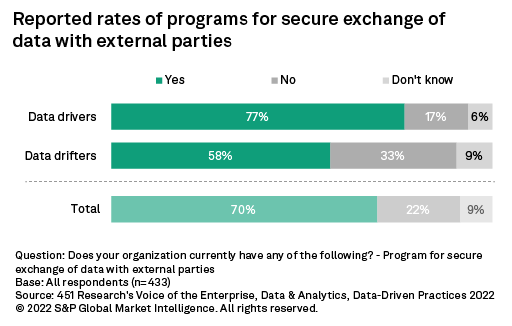
Organizations that already depend heavily on data for decision-making are more likely to have consistent methods to secure that data. And while the differences between data drivers and data drifters are perhaps not surprising, other patterns emerge as well. Respondents from the financial services industry are the most likely to report a program for the secure exchange of data with external parties — at a rate of 88%. Collaborative anti-fraud and anti-money laundering efforts in the financial services sector often require the sharing of highly sensitive customer financial patterns across industry competitors, where inadvertent exposure of too much information could lead to loss of competitive advantage. That risk drives technological innovation.
Organizations might be overestimating their secure external exchange capabilities
High confidence in the presence of a secure external data exchange program does not necessarily translate into consistency of technological capabilities across organizations. Reported rates of secure data exchange programs are surprisingly high, especially when examined in context with the reported rates of other programs and technologies associated with data-driven practices within the walls of the organization.
Today, only a slight majority (58%) of total survey respondents report their organization has a self-service data catalog, and barely half (51%) report that their organization has a self-service data marketplace or exchange, with both approaches representing examples of how data is commonly served to and managed for workers inside the business. In broader data management trends, usually, internal practices and supporting technology for internal data culture are more advanced than the supporting mechanisms associated with collaboration with external parties. In other words, organizations usually focus on the development of their own data management and data security infrastructure internally before they can expect to do so consistently working with other parties. Yet adoption rates for these "internal" data access and collaboration methods are surprisingly lower than reported rates for secure external data exchange programs.
One reason for this may be an overestimation of secure external data exchange capabilities, with rudimentary secure data transfer methods being over-reported as a method of secure external data exchange. With secure file transfer protocol, or FTP, long available, many organizations may mistake secure transfer for a secure data exchange and sharing program. Yet securing the point-to-point transfer of a dataset does nothing to protect the visibility or processing of data once it is received, undermining the overarching objective of secure external data collaboration. Likewise, rudimentary techniques such as password protection or one-way encryption for datasets only provide the keys to the kingdom for those that receive it, generally doing nothing granular to protect the sensitivity of individual fields or values.
Evolution toward more advanced secure external data exchange
Businesses generally obtain and process datasets to derive actionable insight, not because any single data point has inherent value in isolation. The same logic holds true for external parties that need to exchange datasets with partners; the outcome needs to be a finding that can drive a mutually beneficial business decision. Increasingly, with evolving data security technology, these insights can be enabled without exposing individual data points.
This is particularly valuable for external data exchange and sharing programs, where exposure of individual fields of data or individual data points could be competitively detrimental to the originating party providing the dataset. Technologies such as various encryption-in-use techniques, methods to abstract and anonymize individual customer data profiles, as well as embedded situationally aware data security controls that "travel" with individual documents and data, can be useful for sharing purposes so that accurate processing and insights are enabled while protecting the privacy and security of the underlying data itself.
The future of secure external data exchange and sharing likely points toward more advanced methods that focus on enabling derived insights from data processing while abstracting away direct external access to source data itself. One example of an enabling technology that seeks to do just that is multiparty compute, or MPC. So while organizations today confidently report high rates of "secure" external data exchange programs, there is likely room for ample growth in this supporting technology market as organizations increase their program sophistication.
Today's high organizational rates of affirming the adoption of secure external data exchange programs should likely be taken with a grain of salt but should also be considered an overall promising sign of awareness of the urgent importance of data security. Generally speaking, the survey results bode well for information security and especially for technology providers that help provide mechanisms for secure collaboration and processing of data between parties.
This article was published by S&P Global Market Intelligence and not by S&P Global Ratings, which is a separately managed division of S&P Global.